Electronic Warfare & Countermeasures
Electronic warfare (EW) systems aim to control, exploit, or deny the enemy's use of the electromagnetic spectrum. These techniques include electronic countermeasures (ECM), electronic support measures (ESM), and electronic attack (EA), deployed to disrupt enemy communications, radar systems, and other electronic equipment. EW plays a critical role in defense applications by enhancing situational awareness, protecting friendly forces, and degrading enemy capabilities, thereby shaping the battlefield in favor of the user.Electronic warfare (EW) is defined by the US Department of Defence’s Dictionary of Military Terms as: “(a)ny military action involving the use of electromagnetic and directed energy to control the electromagnetic spectrum, or to attack the enemy”.
Electronic warfare includes three subdivisions: Electronic Attack, Electronic Protection and Electronic Support subordinate missions.
Electronic Attack (EA) harnesses electromagnetic energy, principally Radio Frequency (RF) signals, against hostile radio-dependent systems and capabilities. These systems and capabilities include radar, communications systems and networks and radio navigation systems.
Electronic Protection (EP) focuses on the protection of one’s own, and friendly, radio-dependent systems and capabilities against EA.
Electronic Support (ES) encompasses all activities which are performed to support the EA and EP missions.
The Three Divisions of Electronic Warfare
Electronic Attack (EA)
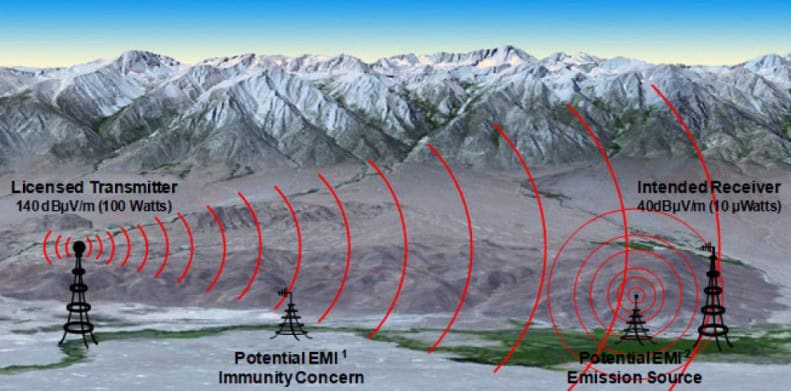
Electronic attack exploits radio signals to attack hostile radars or radios, SATCOM or satellite navigation. This is done to prevent these systems operating. During an air campaign, one air force may use electronic attack against it’s adversary’s Integrated Air Defence System (IADS).
Combat aircraft may carry powerful jammers that direct radio signals against the IADS’ radars. This will aim to prevent those radars detecting the incoming aircraft. With the radars blinded, it will be harder to direct missiles, anti-aircraft artillery or defending fighters towards the incoming aircraft.
Jamming may also be done to disrupt the IADS’ radio communications to prevent the management and coordination of a responses.
Electronic Protection (EP)
Electronic protection is the harnessing of EW to protect against sensors or weapons primarily dependent on radar. When a threat, such as a missile, is detected EW systems begin transmitting jamming signals towards the aggressor’s radar. The intention is to blind the radar to cause the missile to lose its target.
Alternatively jamming may be performed in such a way as to create a false, but more tempting, target in the missile’s radar. The missile may then opt to guide itself towards the fake target, believing it to be more lucrative and affording a better chance of a kill. To an extent, electronic attack and electronic protection are overlapping missions.
Electronic Support (ES)
Electronic support constitutes all activities related to facilitating EW. Electronic warfare depends on the continual collection and analysis of Signals Intelligence (SIGINT).
SIGINT comprises Communications Intelligence (COMINT) on radio communications, SATCOM and radio networks. SIGINT also comprises Electronic Intelligence (ELINT) covering radars. Signals intelligence efforts collect parametric information on radars, SATCOM and radio communications. This includes details of what radio frequencies these systems use, where they are physically located, precise details on the composition of their radio signals and when these systems are active to name just four criteria.
This can be done using a variety of capabilities. These can include SIGINT satellites in space listening to radio emissions emanating from Earth. It can also be done using covert vehicle or backpack SIGINT systems surreptitiously moving around a city. SIGINT enables electronic attack and electronic protection tactics to then be devised and implemented.
Cyber & Electromagnetic Activities (CEMA)
The advent of cyberwarfare has given electronic attack an additional mission. Alongside jamming, electronic attack signals can be loaded with malicious code. This code can be injected into a hostile radar, radio or SATCOM terminal via an electronic attack. This may be done to attack these specific systems. Alternatively, it can be done to gain access to the communications networks they are connected to. This could allow the cyberattack to spread to targeted computers on that network.
If attacking a hostile Integrated Air Defence System hostile (IADS), a cyberattack could be injected through a radar. It may leave the radar alone but spread through networks targeting computers controlling the IADS. This has resulted in a morphing of EW terminology, in some cases, to reflect this new mission. As a result, terms such as CEMA (Cyber and Electromagnetic Activities) and EMSO (Electromagnetic Support Operations) have evolved to encompass the EW and cyber missions.
Products (22)
Related Articles
Rugged High Performance Computing & Video I/O Modules: 6U and 3U VPX, and XMC for Defense Applications

Advanced Solutions for Defense Modernization: Propulsion, Sensors, Communication & Augmented Reality Systems

Assured Position, Navigation and Timing (PNT) Solutions for Military and Defense
Cutting-Edge AI-Powered Cybersecurity Threat Management Solutions for Embedded Computers Within Military & Defense Systems

High Reliability Solutions for Managing the Electromagnetic Spectrum

Cutting-Edge Encryption Solutions for Military & Government: Protection Against The Most Sophisticated Modern Cyber Threats
Electronic Countermeasures (ECM) & RF Jamming Technology for Protection from RCIED and Drone Threats
Assured PNT Solutions for Mission Critical Military, Defense & Government Applications