Modern military drones are advanced platforms that depend on tightly integrated software, embedded systems, navigation modules, and communication interfaces. These systems enable autonomous operations, real-time data transfer, and mission-critical decision-making. However, their reliance on digital infrastructure makes them vulnerable to an expanding set of cybersecurity threats.
Drone Cybersecurity Solutions
Drone cybersecurity has emerged as a critical focus in the defense sector, where unmanned aerial systems (UAS) are increasingly exposed to a growing array of cyber threats. From embedded computers and navigation systems to communication links and AI-driven software, every onboard component of a drone is a potential attack surface. As military and tactical drones become more sophisticated, so do the cyber-physical attacks aimed at compromising their performance, misdirecting missions, or stealing sensitive data. This category explores the evolving cybersecurity landscape for drones, focusing on the software solutions and protective measures designed to secure embedded systems and thwart adversarial exploitation.Understanding the Drone Attack Surface
Drones are particularly susceptible to cyberattacks due to their reliance on interconnected digital components. Their attack surface includes embedded computers, flight control systems, GPS-based navigation, wireless communications, onboard sensors, and artificial intelligence software. These systems can be targeted independently or in combination to disrupt drone performance or control.
The three primary vulnerabilities in drone-based systems are:
- Embedded systems: These are often built on real-time operating systems (RTOS) and may not include hardened security protocols by default. Attackers can exploit firmware vulnerabilities or gain unauthorized access via physical or wireless interfaces.
- Navigation systems: GPS spoofing and GPS jamming are among the most common techniques used to mislead drones or force them into failure states.
- Communications: Unsecured data links between drones and control stations are prone to interception, replay attacks, and man-in-the-middle attacks, risking control and data integrity.
Types of Cyber Attacks on Drones
Cyber attacks on drones range from basic signal interference to sophisticated software-based exploitation. These attacks can be executed remotely or from nearby physical locations, and often target the embedded computing infrastructure responsible for controlling and guiding the UAV.
1. Denial of service (DoS) and distributed denial of service (DDoS) attacks
DoS and DDoS attacks flood a drone’s communication channels or onboard systems with traffic, overwhelming its processing capabilities. These attacks can shut down command links, rendering the drone unresponsive or forcing emergency landings.
2. GPS spoofing and jamming
Adversaries can manipulate a drone’s perceived location by sending false GPS signals (spoofing) or blocking GPS reception entirely (jamming). GPS spoofing is particularly dangerous in military drones, as it can redirect them or make them believe they have reached a target when they have not.
3. Replay and man-in-the-middle attacks
By capturing and retransmitting previously recorded communication packets, attackers can execute replay attacks that trick drones into accepting false commands. In a man-in-the-middle attack, the attacker intercepts and potentially alters communications between the drone and its operator.
4. Software exploitation and zero-day vulnerabilities
Attackers exploit bugs in a drone’s operating system or mission software, often through zero-day vulnerabilities unknown to developers. Such exploits can allow attackers to bypass authentication, install malware, or gain root access to embedded systems.
5. Signal jamming and interference
Beyond GPS, other critical radio frequencies used for telemetry, video transmission, or control can be jammed. These brute-force methods may not be subtle, but they effectively cut off a drone from its control infrastructure.
6. Malware injection
Through physical access, over-the-air updates, or unsecured interfaces, malware can be introduced to drones. This allows persistent access for adversaries, data exfiltration, or disruptive behavior.
7. Side-channel and brute-force attacks
Advanced attackers may employ side-channel techniques that analyze power usage or electromagnetic leaks to deduce cryptographic keys or internal logic. Brute-force attacks on poorly secured interfaces or passwords are also possible when drones use default or weak credentials.
8. Cyber-physical attacks
These attacks go beyond data manipulation, aiming to induce physical harm or disruption through software. For example, a cyber-physical attack may cause a drone to overheat, overload motors, or take dangerous flight paths.
Protecting Embedded Systems in Drones
Given the mission-critical nature of military UAVs, safeguarding embedded computers is a top priority. Modern drone cybersecurity solutions use multiple layers of defense to harden these systems against compromise.
Hardware security modules (HSMs) and secure boot protocols ensure that only authenticated firmware and software are executed.
Real-time intrusion detection systems monitor for anomalous behavior in embedded systems, such as unauthorized memory access or abnormal power usage.
Encryption of onboard data and communication traffic prevents interception and manipulation, even if systems are accessed.
Drone cybersecurity platforms also implement sandboxing, where mission-critical processes run in isolated environments to prevent lateral movement in case of a breach.
Secure Communications & Navigation
To counteract GPS spoofing, drones can use multi-frequency GPS receivers, inertial navigation systems (INS), and anti-jamming antennas. Combining inputs from multiple navigation sources improves resilience and accuracy.
For secure communication, drones increasingly rely on frequency-hopping spread spectrum (FHSS), encrypted data links, and authenticated protocols that resist replay and man-in-the-middle attacks. AI software also dynamically adapts communication protocols to perceived interference or jamming.
AI-Driven Threat Detection & Response
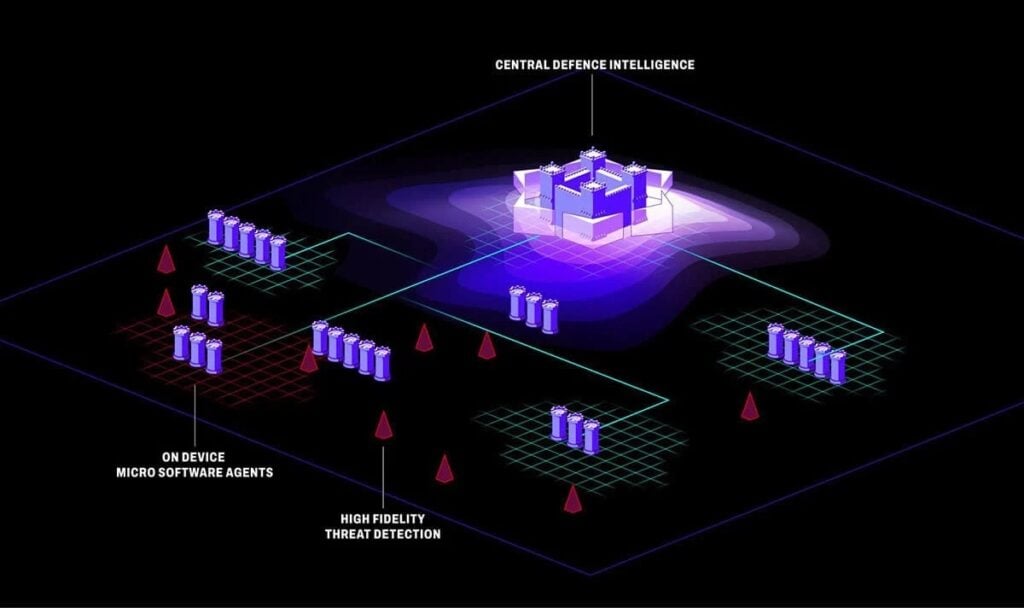
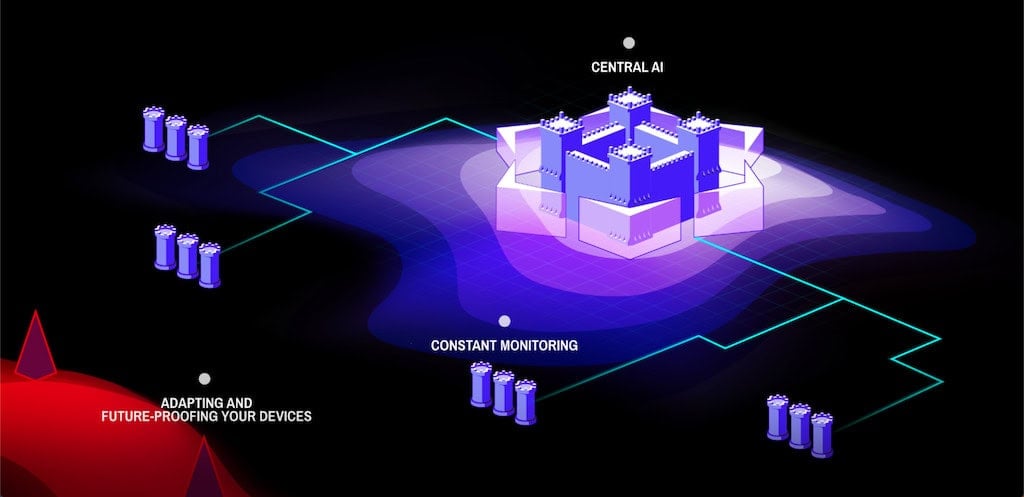
AI software plays a growing role in drone cybersecurity threat management. These systems analyze telemetry, control signals, and sensor inputs to detect patterns indicative of a cybersecurity threat. Upon detection, AI can autonomously execute mitigation strategies, rerouting missions, isolating compromised components, or initiating return-to-base protocols.
AI can also simulate potential attack scenarios in real time, allowing drones to prepare and adapt before real threats materialize.
Drone Cybersecurity Solutions & Platforms
Multiple vendors now offer comprehensive drone cybersecurity platforms for military and enterprise applications. These platforms often include:
- Endpoint protection for embedded computers
- Secure firmware update capabilities
- Encrypted command and control frameworks
- Real-time behavioral analytics and anomaly detection
- Threat intelligence integration for proactive defense
- Defense integrators may also deploy cybersecurity threat mitigation tools at the network level, protecting not only the UAVs but also the ground control stations and communication infrastructure
Challenges in Implementation
Despite advancements, drone cybersecurity risk mitigation remains complex. The limited size, weight, and power (SWaP) budgets of tactical drones restrict the addition of robust security hardware. Additionally, real-time operational requirements mean heavy encryption or processing-intensive solutions may degrade performance.
Balancing security with functionality requires optimized cybersecurity solutions that are purpose-built for constrained embedded environments.
Future Outlook for Drone Cybersecurity
As military and tactical drones evolve with more autonomous functions and AI-driven decision-making, their cybersecurity posture must evolve in parallel. Regulatory frameworks and standardized certifications for drone cybersecurity solutions for enterprises and governments will likely emerge.
Collaboration between defense agencies, cybersecurity vendors, and embedded systems developers will be essential to keep pace with adversaries employing increasingly sophisticated techniques, from software exploitation to advanced cyber-physical attacks.
Drone cybersecurity is a vital defense priority, particularly for systems reliant on embedded computers, GPS navigation, and wireless communication. As drones play critical roles in military operations, the range of cyber threats, spanning GPS spoofing, DDoS attacks, malware injection, and zero-day exploits, demands advanced protection strategies. Integrated software platforms, AI-based detection, and secure-by-design embedded systems offer the most robust path forward. Ensuring resilience against evolving threats will be central to maintaining the strategic and tactical effectiveness of modern UAVs.
Products (2)
Related Articles

Rugged High Performance Computing & Video I/O Modules: 6U and 3U VPX, and XMC for Defense Applications
Cutting-Edge AI-Powered Cybersecurity Threat Management Solutions for Embedded Computers Within Military & Defense Systems

Cutting-Edge Encryption Solutions for Military & Government: Protection Against The Most Sophisticated Modern Cyber Threats