Cybersecurity for embedded systems in unmanned platforms has emerged as a decisive factor in ensuring mission integrity and operational safety. Unlike conventional IT environments, embedded systems in unmanned ground vehicles (UGV) and unmanned aerial vehicles (UAV) are tightly constrained in power, weight, and processing capacity, often operating in contested or remote environments. This combination of limitations and exposure makes them attractive targets for exploitation and thus demands robust, purpose-built embedded cybersecurity solutions.
Embedded Cybersecurity for Drones and Unmanned Systems
As unmanned platforms evolve to perform more autonomous and mission-critical roles, their embedded computing components face growing exposure to sophisticated cyber threats. Whether deployed on land or in the air, unmanned systems depend on secure, resilient embedded architectures to maintain functionality, ensure data integrity, and prevent adversarial control. Hardware-rooted trust, tamper resistance, and lightweight cryptography are no longer optional; they are fundamental to safeguarding autonomous and remote operations.What is Embedded Cybersecurity?
Embedded cybersecurity refers to protecting computing systems that are integrated into hardware and perform dedicated functions within larger mechanical or electrical systems. In unmanned systems, this includes the processors, sensors, controllers, and software that govern navigation, communication, and decision-making processes. Embedded system security combines hardware and software-based mechanisms to defend against firmware tampering, data leakage, and unauthorized remote access.
Securing Embedded Computing in Unmanned Systems
Unmanned ground vehicles and unmanned aerial systems rely on embedded architectures that are mission-critical and often exposed to adversarial environments. This necessitates the implementation of layered security protocols:
- Secure boot and firmware validation: Ensures that only verified code is executed on power-up, blocking malicious or corrupted software at the earliest stage.
- Cryptographic hardware modules: Provide hardware-based encryption and key storage to protect communications and system data.
- Real-time operating system (RTOS) hardening: Limits vulnerabilities in time-sensitive software environments, reducing the attack surface.
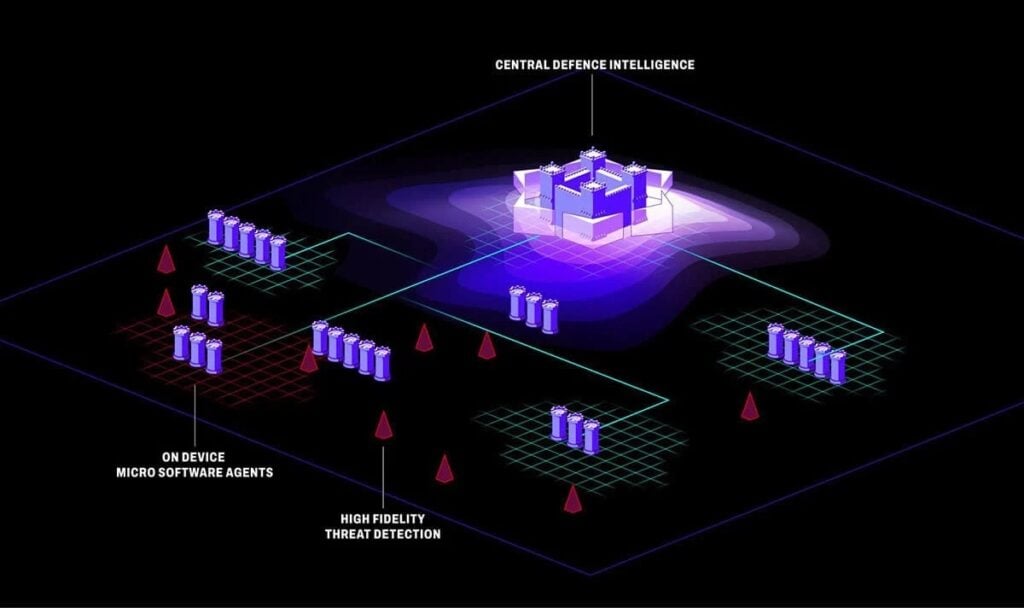
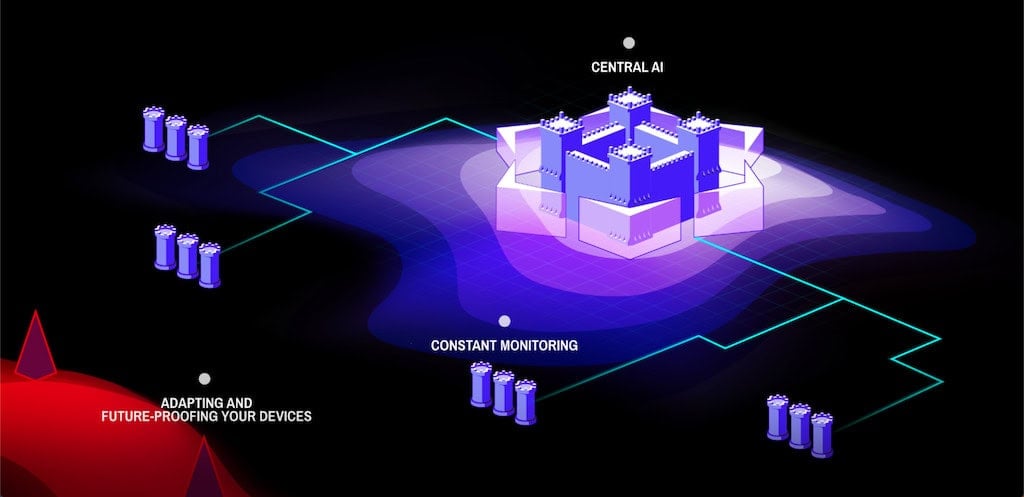
- Intrusion detection and anomaly monitoring: Embedded systems can integrate lightweight sensors that detect unexpected behavior or external probing.
By embedding these features directly into the computing hardware and firmware, developers ensure that security is not a bolt-on feature but an intrinsic property of the system.
Application in Unmanned Aerial and Ground Systems
UAS and UGVs frequently conduct missions that involve surveillance, reconnaissance, or logistics in sensitive or contested zones. These operations generate high-value data and often depend on persistent communications with control stations or peer vehicles. Embedded system security measures ensure the confidentiality and integrity of these operations.
In aerial platforms, embedded cybersecurity helps protect avionics and navigation software from spoofing or manipulation. In ground vehicles, it secures vehicle control units and autonomy stacks against local or network-based interference. Since unmanned systems often operate autonomously or semi-autonomously, the stakes of a security breach are heightened, posing potential risks not only to data but also to safety and physical integrity.
Challenges and Trends in Embedded Cybersecurity
Protecting embedded computing in unmanned systems comes with unique constraints. These systems may have limited processing overhead for traditional cybersecurity software and often must operate for long durations without human oversight or internet access. Therefore, embedded cybersecurity solutions must be lightweight, efficient, and capable of functioning autonomously.
Recent advances include the integration of AI-driven threat detection directly into embedded systems and the use of secure enclaves or Trusted Execution Environments (TEEs) for isolating sensitive operations. In tandem, secure software supply chain practices are gaining attention, ensuring that third-party code or updates do not introduce vulnerabilities into the system.
The increasing adoption of open standards and modular architectures supports a more agile cybersecurity posture, allowing system integrators to adapt embedded security strategies to evolving threats and new platform requirements.
A Unified Approach to Embedded System Cybersecurity
As UAS and UGV technologies converge with edge computing and AI-driven autonomy, the line between hardware and software security continues to blur. Effective cybersecurity for embedded systems must encompass everything from silicon-level defenses to system-wide patching strategies and secure over-the-air updates.
System integrators, OEMs, and defense contractors prioritize embedded security as a core design requirement rather than a post-deployment addition. This includes collaboration across chipmakers, software vendors, and cybersecurity specialists to ensure that each layer of the technology stack is resilient against known and emerging threats.
Summary of Embedded Cybersecurity
The safeguarding of embedded computing in unmanned systems is fundamental to the reliability and security of modern defense platforms. Embedded cybersecurity solutions, from secure boot mechanisms to real-time monitoring, fortify UGVs and UAS against cyber threats without compromising performance or autonomy. As these platforms take on increasingly critical roles in defense operations, their embedded systems must be protected by design, adaptable to future threats, and certified to the highest standards of embedded system security.
Products (9)
Related Articles
Cutting-Edge AI-Powered Cybersecurity Threat Management Solutions for Embedded Computers Within Military & Defense Systems

Cutting-Edge Encryption Solutions for Military & Government: Protection Against The Most Sophisticated Modern Cyber Threats